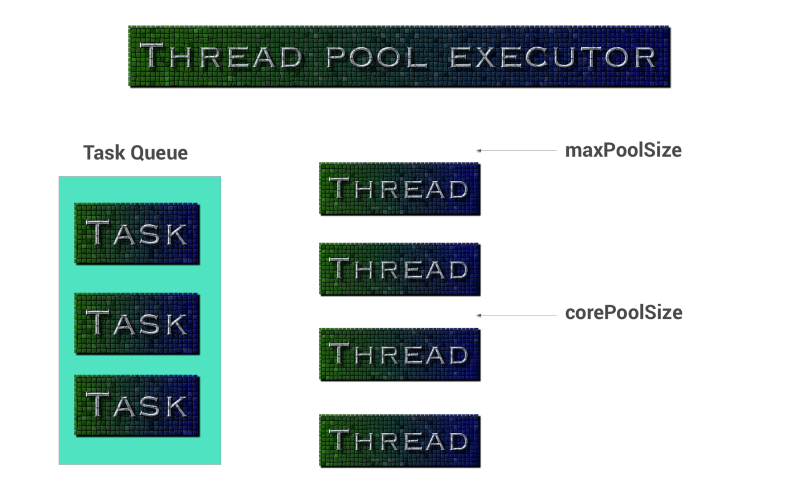
这篇文章将涉及到线程池,线程池执行程序,和他们在Android中的使用。
我们将使用很多的利用,详细的(thoroughly)介绍这些主题。

这篇文章将涉及到线程池,线程池执行程序,和他们在Android中的使用。
我们将使用很多的利用,详细的(thoroughly)介绍这些主题。
昨天开始封装一个安卓多线程下载器,在写的过程中,猜测想加入检测下载过程中的速度,于是google一番,得出一个比较靠谱的答案,在此总结一下。
调用系统相机,拍照:
Intent intent = new Intent(MediaStore.ACTION_IMAGE_CAPTURE);
getFileUri();
intent.putExtra(MediaStore.EXTRA_OUTPUT, file_uri);
startActivityForResult(intent, CODE_CAMERA);
private void getFileUri() {
image_name = Calendar.getInstance().getTimeInMillis() + ".jpg";
file = new File(Environment.getExternalStoragePublicDirectory(Environment.DIRECTORY_PICTURES) + File.separator + image_name);
file_uri = Uri.fromFile(file);
}
Ten soldiers were setting up tents in the forest preparing for the night.
Later, two thieves arrived and attempted to rob them of their rations, but were caught.
The soldiers told them, "We would kill you, but we're in a good mood today.
We'll release you if you can make us all laugh." The thieves reluctantly agreed.
One begins to tell a humorous story.
After the story, nine of the soldiers are laughing hysterically.
However, one is merely looking at the thief with a blank stare.
Consequently, one soldier told the thief "Sorry, not all of us laughed," and killed him.
The other thief was nervous after seeing his friend killed, so he told a much less entertaining story.
No soldiers were laughing except for the one who didn't laugh previously, so they killed the second thief as well.
After killing the thieves, the soldiers asked their friend, "Why did you laugh during the second thief's story but not during the first's?
It was much funnier after all."
He responded, "When the second thief was speaking, I finally understood the first thief's story, and it was damn funny."
引用Zootopia(疯狂动物城)的一个场景,so hilarious!:

只需将form的action 设置为<?php echo $_SERVER['PHP_SELF'];?>
为了防止跨站点攻击(XSS),我们通常需要使用htmlspecialchars()
避免$_SERVER[“PHP_SELF”] 被利用。如下:
<form method="post" action="<?php echo htmlspecialchars($_SERVER["PHP_SELF"]);?>">
- 原文链接 [https://docs.oracle.com/javase/tutorial/java/generics/index.html)
- 翻译: Adamin90
- 转载请注明出处,谢谢!
在任何繁琐的(nontrivial)软件项目中,bug是家常便饭。细心的规划,编程和测试可以帮助减少bug的普遍性(pervasiveness),但是无论如何,无论在哪里,bug总会伺机悄悄溜进(creep)你的代码,因为很明显,新的特性会不断的被引入,并且你的代码基数会不断变大和复杂。
幸运的是,一些bug相比其它比较容易检测。编译时bug可以在早期被检测到;你可以利用编译器的错误信息查明是什么问题并且解决,就在那时。然而,运行时bug会更加未预知,他们不会立即展示出来,不知道什么时候发生,可能根本不在程序真正出现问题的点上。
泛型通过更多的在编译时检测bug为你的代码增加了稳定性。
use one day for establish this blog,thanks for opensource!
Now we can say good night!
``